Denial-of-service (DOS) attacks and distributed denial-of-service (DDOS) attacks are two of the most common cyber threats encountered by businesses and individuals.
While the two may seem interchangeable, there are significant differences between the two types of attacks.
In this section, we will explore the intricacies of DOS and DDOS attacks, discussing their differences, impact and prevention methods.
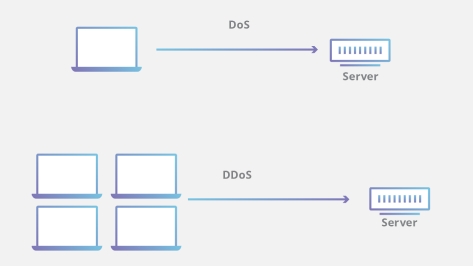
DOS attacks involve a single source attacking a target system with overwhelming traffic or requests, causing the system to shut down or render it inaccessible.
DDOS attacks, on the other hand, utilize multiple sources to launch a coordinated assault on a target system or network simultaneously.
This makes DDOS attacks much more challenging to prevent and defend against.
The impact and consequences of DOS and DDOS attacks can be severe and far-reaching.
For businesses, these attacks can result in prolonged system downtime, loss of revenue, damage to reputation and the possibility of data breaches.
Individuals may encounter disruptions to their online activities and the potential loss of personal information.
It is crucial to understand the potential impact and risks associated with these attacks to take proactive measures to mitigate them.
Preventing DOS and DDOS attacks requires a multi-faceted approach.
This includes implementing firewalls, intrusion detection systems and load balancers.
Regular monitoring of networks, keeping software up to date and educating employees to recognize and report suspicious activities can help prevent and mitigate these attacks.
By understanding the differences between DOS and DDOS attacks and implementing effective prevention measures, businesses and individuals can protect their systems and networks from potential disruptions.
Stay informed and prioritize the security of your digital infrastructure to prevent dos vs ddos attack from targeting your system or network.
The Difference Between DOS and DDOS Attacks
Denial-of-Service (DOS) attacks and Distributed Denial-of-Service (DDOS) attacks are two commonly used terms in the cybersecurity landscape.
Both types of attacks can cause significant disruptions to a targeted system or network, but they differ in their scale and execution.
The Basics of a DOS Attack
A DOS attack is a type of cyber attack that involves a single source overwhelming a target with traffic or requests.
This can cause the server to crash or become unresponsive, resulting in a denial of service for legitimate users.
DOS attacks can be executed in various ways, including sending malformed packets, exploiting vulnerabilities in the server software or overwhelming the system with requests.
Small-scale DOS attacks can typically be mitigated by implementing basic security measures, such as firewalls and intrusion detection systems.
However, more sophisticated attacks can be more challenging to defend against.
The Basics of a DDOS Attack
A Distributed Denial-of-Service (DDOS) attack involves multiple sources working together to launch a coordinated assault on a target.
These sources can be compromised devices that are part of a larger network, known as a botnet.
DDOS attacks are more challenging to defend against than DOS attacks because they come from multiple sources, making it difficult to identify and block all of the traffic.
Additionally, the attackers can change the source of the attack, making it more challenging to locate and shut down the source.
DDOS attacks can have varying levels of intensity, with some being able to generate traffic volumes exceeding hundreds of gigabytes per second.
Overall, DOS attacks are typically smaller in scale and involve a single source, while DDOS attacks are more extensive and involve multiple sources working together.
To defend against these types of attacks, it is essential to have a solid understanding of the difference between the two and implement appropriate preventive measures.
Now that we’ve covered the basics, let’s take a closer look at the impact and consequences of DOS and DDOS attacks in the next section.
The Impact and Consequences of DOS and DDOS Attacks
DOS and DDOS attacks can have devastating effects on businesses and individuals alike.
Understanding the potential impact is essential for recognizing the significance of taking preventative measures.
Loss of Productivity
One of the most significant consequences of a DOS or DDOS attack is the loss of productivity caused by system downtime.
During an attack, the targeted system or network becomes overwhelmed, making it virtually impossible for legitimate users to access it.
This can result in prolonged downtime, which disrupts critical business operations and leads to a loss of revenue.
Damage to Reputation
Another consequence of DOS and DDOS attacks is damage to the reputation of the targeted organization.
In the event of a successful attack, customers may view the organization as being unreliable, unsafe or untrustworthy.
This can impact the affected organization’s ability to win new business, retain existing customers and maintain its market position.
Data Breaches
DOS and DDOS attacks can also lead to data breaches, particularly when the attacks are used as a smokescreen to distract security personnel.
During the chaos caused by an attack, hackers may attempt to exploit vulnerabilities in the targeted system or network, gain unauthorized access, and exfiltrate sensitive data.
This can result in significant legal, financial and reputational consequences for the affected organization.
By understanding the potential impact of DOS and DDOS attacks, organizations can take proactive measures to safeguard against them.
Preventing DOS and DDOS Attacks
Preventing DOS and DDOS attacks requires a multi-faceted approach to mitigate the risks associated with these types of attacks. Effective strategies include:
- Implementing firewalls: Firewalls act as a protective barrier between your internal network and the internet, analyzing incoming traffic and blocking potentially harmful requests.
- Intrusion detection systems: These systems monitor network traffic for suspicious activity and alert administrators in case of an attack.
- Load balancers: Load balancers distribute incoming network traffic evenly across multiple servers, preventing any one server from becoming overwhelmed.
Regular network monitoring is also crucial for identifying and responding to potential threats in real-time.
Keeping software up to date is essential, as cyber attackers often target known vulnerabilities in outdated software.
It’s also essential to educate employees on the importance of recognizing and reporting any suspicious network activity.
Preventing DOS and DDOS Attacks
Implementing the following measures can help prevent DOS and DDOS attacks:
- Deploying intrusion prevention systems: These systems monitor network traffic and can automatically block suspicious activity before it reaches your network.
- Limiting network access: Limiting network access to only necessary personnel can prevent unauthorized access and reduce the risk of an attack.
- Using content delivery networks (CDNs): CDNs can distribute incoming traffic across multiple servers, lowering the impact of any one server becoming overwhelmed.
By implementing these prevention measures and staying informed about evolving attack techniques, businesses and individuals can safeguard their systems and networks against potential disruptions.
Conclusion
Denial-of-service (DOS) and distributed denial-of-service (DDOS) attacks are serious threats that can cause significant damage to businesses and individuals.
It is crucial to understand the differences between the two types of attacks in order to implement effective prevention measures.
By utilizing firewalls, intrusion detection systems and load balancers, businesses can help prevent attacks from overwhelming their systems.
Regular network monitoring and software updates can also help keep networks secure.
However, it is important to remember that prevention is an ongoing process and education and awareness are vital to staying protected.
By staying informed about evolving attack techniques and taking proactive measures to safeguard digital infrastructure, individuals and businesses can reduce the risk of being targeted by DOS and DDOS attacks.
Remember to prioritize the security of your systems and networks to ensure business continuity and protect sensitive information from potential breaches.
FAQ
What is the difference between a DOS attack and a DDOS attack?
A DOS attack involves a single source overwhelming a target with traffic or requests, while a DDOS attack utilizes multiple sources to launch a coordinated assault.
What are the consequences of DOS and DDOS attacks?
DOS and DDOS attacks can lead to prolonged system downtime, loss of revenue, damage to reputation, and potential data breaches.
How can I prevent DOS and DDOS attacks?
Effective prevention strategies include implementing firewalls, intrusion detection systems, load balancers, regular network monitoring, keeping software up to date, and educating employees to recognize and report suspicious activities.
Why is it important to understand the difference between DOS and DDOS attacks?
Understanding the difference allows for the formulation of an effective defense strategy and enables businesses and individuals to safeguard their systems and networks against potential disruptions.
How can I prioritize the security of my digital infrastructure?
By implementing the appropriate prevention measures, staying informed about evolving attack techniques, and prioritizing the security of your digital infrastructure, you can better protect your systems and networks.