In the realm of cybersecurity, safeguarding sensitive data during online communication is paramount.
IPsec, or Internet Protocol Security, plays a vital role in ensuring the confidentiality and integrity of data transmitted over networks.
But what are the 3 main protocols that IPsec uses to achieve this?
In this in-depth article, we’ll explore these protocols, their functions, and how they contribute to secure online communication.
IPsec: The Guardian of Online Security
IPsec is like the guardian angel of your online data.
It stands as a shield between your information and potential threats, providing a secure tunnel for data transmission.
Let’s delve into the 3 main protocols that IPsec employs for this mission:
Authentication Header (AH)
The Authentication Header, or AH, is one of the three pillars of IPsec.
Its primary role is to ensure data integrity and authenticity.
When AH is in use, it adds a digital signature to each data packet, allowing the recipient to verify that the data hasn’t been tampered with during transmission.
AH also prevents replay attacks, where an attacker intercepts and retransmits data packets to gain unauthorized access.
By including a sequence number in the header, AH ensures that each packet is unique.
- Data Integrity: AH uses cryptographic algorithms to create a checksum of the data. Any alteration in the data will result in a different checksum, alerting the recipient to potential tampering.
- Authentication: AH provides authentication through digital signatures, verifying the sender’s identity.
- Replay Attack Prevention: By using sequence numbers, AH safeguards against replay attacks.
Encapsulating Security Payload (ESP)
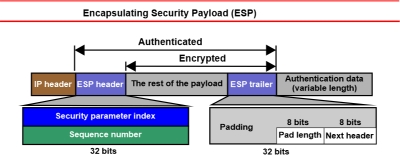
The Encapsulating Security Payload, or ESP, is another cornerstone of IPsec.
While AH focuses on integrity and authentication, ESP adds an extra layer of security through encryption.
It ensures that even if malicious actors intercept the data, they won’t be able to decipher it.
- Data Encryption: ESP employs encryption algorithms to scramble the data, making it unreadable without the decryption key.
- Data Authentication: Similar to AH, ESP also provides data authentication to confirm the sender’s identity.
- Confidentiality: With ESP, your data remains confidential and secure from prying eyes.
Security Associations (SAs)
Security Associations, or SAs, are essential in IPsec.
They define the rules and parameters for secure communication between two devices.
Every IPsec connection establishes one or more SAs to govern the exchange of data.
- Negotiation: Devices negotiate SAs to determine the security parameters, such as encryption algorithms and keys.
- Security Context: SAs store the information needed for secure communication, including cryptographic keys and security protocols.
- Bidirectional Communication: SAs enable bidirectional communication by specifying rules for both outgoing and incoming data.
FAQs
Is IPsec only used for securing internet communication?
No, IPsec can be used for securing communication over any IP-based network, including private networks.
Can I use IPsec on my smartphone?
Yes, many smartphones support IPsec for secure communication, especially in corporate environments.
Is IPsec vulnerable to brute force attacks?
IPsec is designed to withstand brute force attacks, provided strong encryption keys are used.
Are there any downsides to using IPsec?
While IPsec enhances security, it can add some overhead to network performance due to encryption and decryption processes.
Can IPsec protect against all types of cyber threats?
While it provides robust security, IPsec should be used in conjunction with other security measures for comprehensive protection.
Are there any open-source implementations of IPsec?
Yes, there are open-source implementations like StrongSwan and OpenSwan that make it accessible to a wide range of users.
Conclusion
In the ever-evolving landscape of cybersecurity, understanding the 3 main protocols that IPsec uses is crucial. AH, ESP, and SAs work together harmoniously to provide data integrity, authentication, encryption, and secure communication.
By incorporating IPsec into your network infrastructure, you can fortify your defenses against online threats and ensure that your data remains confidential and secure.
Remember, in the digital age, security is paramount.
IPsec is your steadfast ally in the ongoing battle to protect your data from cyber threats.
So, embrace these protocols and secure your online world with confidence.






