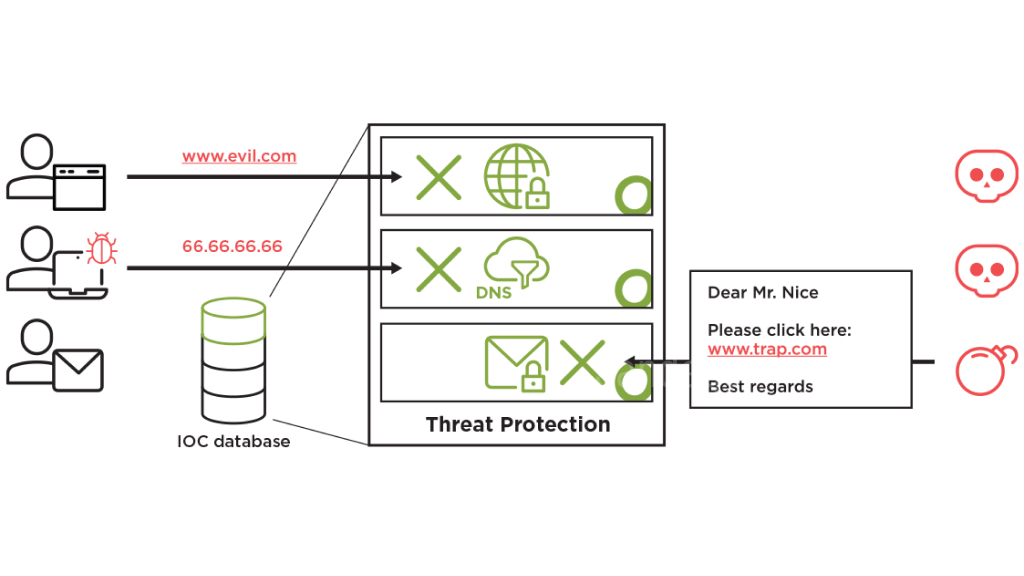
Welcome to our article on advanced threat protection and the significance of cybersecurity solutions. With the ever-rising prevalence of sophisticated cyber threats, safeguarding your digital environment has become more crucial than ever. This article explains the fundamentals of advanced threat protection and its pivotal role in protecting your system from cybercriminals.
In this guide, we will explore the various cybersecurity solutions that enable you to effectively protect against advanced threats. We will discuss the importance of network security, threat intelligence, malware detection, endpoint security, and cloud security. Our aim is to provide a comprehensive understanding of how to safeguard your digital environment from the ever-growing risk of cybercrime.
The Basics of Advanced Threat Protection
Advanced threat protection is essential to safeguard your digital environment against sophisticated cyber threats. However, before we dive into its importance, let’s first discuss the basics. One critical component of advanced threat protection is network security.
Network security helps detect and prevent advanced threats, which can infiltrate your systems through various means, including phishing attacks, social engineering, and unpatched vulnerabilities. Network security solutions often include firewalls, intrusion detection systems, and secure gateway controls.
In addition to network security, other key components of advanced threat protection include:
- Threat intelligence – providing real-time information on emerging threats and attack vectors, enabling organizations to stay ahead of cyber threats.
- Malware detection – identifying and neutralizing malicious software, which can cause significant damage to your systems and data.
By implementing these components, organizations can protect their networks and systems from the increasingly sophisticated tactics used by cybercriminals, who may be seeking to steal sensitive data or disrupt operations.
For further protection, a comprehensive approach to network and endpoint security is essential. This includes continuous monitoring, strong access controls, and regular employee training to raise awareness of potential threats and minimize the risk of human error resulting in a breach.
Stay ahead of the curve by investing in advanced threat protection and keeping your systems and data secure from cyber threats.
Understanding Threat Intelligence
Threat intelligence is an essential component of advanced threat protection strategy. It refers to the knowledge and insights gained from analyzing data on emerging cyber threats and attack vectors. Threat intelligence helps organizations stay ahead of cyber threats by providing real-time, actionable information on potential security risks.
There are two types of threat intelligence: strategic and tactical. Strategic intelligence focuses on analyzing long-term trends and identifying key threat actors, while tactical intelligence provides real-time insights into specific threats and attack patterns. Both types of threat intelligence are crucial in developing an effective advanced threat protection plan.
To gather threat intelligence, organizations may use a variety of sources, including open-source intelligence, social media, and dark web monitoring. The information is then analyzed to identify potential security threats and vulnerabilities. With the help of threat intelligence, organizations can proactively take steps to prevent cyber attacks and minimize the impact of any successful attack.
Protecting Against Malware and Ransomware
Malware and ransomware are two of the most prevalent cyber threats that can cause serious damage to an organization’s digital environment. Advanced threat protection solutions provide robust defenses against these threats by detecting and mitigating them in real-time.
To protect against malware attacks, advanced threat protection solutions use a variety of sophisticated techniques such as signature-based scanning, behavioral analysis, and sandboxing. These techniques help detect and prevent the infection of endpoints and network devices.
Similarly, ransomware prevention requires a multi-layered approach that includes robust backup and recovery processes, user education, and advanced threat protection solutions. By using these techniques, organizations can reduce the impact of a ransomware attack and avoid paying the ransom demanded by cybercriminals.
Advanced threat protection solutions can also help organizations to detect and prevent zero-day attacks, which target vulnerabilities that are unknown to the software vendor.
Overall, protecting against malware and ransomware is a critical component of advanced threat protection. By implementing the right strategies and solutions, organizations can ensure the security and integrity of their digital environment.
Securing Cloud and Endpoint Environments
Cloud and endpoint environments have become prime targets for sophisticated cyber attacks. Implementing robust cloud security measures and endpoint security solutions is essential in protecting against advanced threats.
Cloud security involves securing data, applications, and infrastructure in the cloud. Some effective security measures include encrypting data, securing access controls, and implementing network segmentation. Additionally, monitoring network traffic and detecting anomalies can help prevent data breaches in the cloud.
Endpoint security, on the other hand, involves securing endpoints such as laptops, desktops, and mobile devices. Endpoint security solutions can help protect against malware, ransomware, and other advanced threats by providing real-time threat intelligence and behavioral analysis. Some examples of endpoint security solutions include antivirus software, firewalls, and intrusion detection systems.
By combining effective cloud security and endpoint security solutions, organizations can significantly reduce their risk of falling victim to cyber attacks.
Preventing Data Breaches with Advanced Threat Protection
Data breaches have become a major concern for organizations of all sizes, and the cost of a breach can be staggering. Advanced threat protection plays a crucial role in preventing data breaches by detecting and blocking sophisticated cyber attacks that target sensitive information.
One of the key components of data breach prevention is encryption. By encrypting data at rest and in transit, organizations can ensure that even if sensitive data is compromised, it cannot be read or accessed by unauthorized individuals.
Access controls are another important aspect of data breach prevention. By limiting access to sensitive data to only authorized individuals, organizations can significantly reduce the risk of data breaches. This can include implementing multi-factor authentication, role-based access controls, and regular access reviews.
Continuous monitoring is also critical in preventing data breaches. By monitoring network traffic and user behavior, organizations can quickly detect any suspicious activity and take action to prevent a breach. This can include implementing security information and event management (SIEM) solutions and conducting regular security audits.
Conclusion
As cyber threats continue to evolve, it’s essential for organizations to prioritize advanced threat protection as a crucial component of their cybersecurity solutions. By implementing robust measures to detect and prevent advanced threats, organizations can effectively safeguard their digital environments and sensitive data against unauthorized access.
Investing in advanced threat protection solutions and staying up-to-date with the latest threat intelligence can help organizations mitigate the risks posed by sophisticated cyber attacks. By prioritizing cybersecurity and taking proactive measures, organizations can minimize the impact of cyber threats and maintain the trust of their customers and stakeholders.
In conclusion, advanced threat protection is critical to ensuring the security and integrity of your digital assets. By working with experienced cybersecurity professionals and investing in robust solutions, organizations can effectively protect against advanced cyber threats and safeguard their digital environments.
FAQ
What is advanced threat protection?
Advanced threat protection refers to a set of cybersecurity solutions and strategies designed to protect your digital environment against sophisticated cyber threats. It includes advanced techniques and technologies for detecting, preventing, and responding to advanced threats.
Why is advanced threat protection important?
Advanced threat protection is important because traditional security measures are often insufficient to detect and prevent advanced threats. Advanced threats, such as zero-day exploits and advanced malware, are constantly evolving and can bypass traditional security defenses. Advanced threat protection provides an additional layer of security to safeguard your digital assets.
What are some examples of cybersecurity solutions for advanced threat protection?
Some examples of cybersecurity solutions for advanced threat protection include network security solutions, malware detection systems, threat intelligence platforms, ransomware prevention tools, cloud security measures, and endpoint security solutions.
How does network security contribute to advanced threat protection?
Network security plays a crucial role in advanced threat protection by detecting and preventing threats from entering your network. It includes technologies such as firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS) that monitor network traffic and identify and block malicious activities.
What is threat intelligence, and how does it enhance advanced threat protection?
Threat intelligence refers to actionable information about potential cyber threats, including the tactics, techniques, and procedures (TTPs) used by hackers. It helps organizations stay ahead of evolving threats by providing real-time information on emerging threats and attack vectors. Threat intelligence enhances advanced threat protection by enabling proactive defense measures.
How can organizations protect against malware and ransomware?
Organizations can protect against malware and ransomware by implementing robust malware detection systems and ransomware prevention tools. These solutions use advanced algorithms and behavioral analysis techniques to detect and block malicious software and prevent ransomware attacks from encrypting critical data.
What are some key components of advanced threat protection?
Some key components of advanced threat protection include malware detection systems, threat intelligence platforms, network security measures, endpoint security solutions, encryption techniques, access controls, and continuous monitoring.
How can organizations secure their cloud and endpoint environments?
Organizations can secure their cloud and endpoint environments by implementing robust cloud security measures, such as data encryption, access controls, and regular security updates. Additionally, endpoint security solutions, like antivirus software and endpoint detection and response (EDR) systems, can provide added protection against advanced threats targeting endpoints.
How does advanced threat protection help prevent data breaches?
Advanced threat protection helps prevent data breaches by implementing proactive measures, such as encryption, access controls, and continuous monitoring. These measures safeguard sensitive data from unauthorized access and ensure that any potential breaches are detected and mitigated promptly.